Disclaimer: I by no means encourage criminality or any piracy motion. Be accountable when using torrenting providers.
Despite the fact that most individuals assume that torrenting solely results in malware and threatening letters out of your ISP, that’s not at all times the case.
Whereas the primary query that pops up would at all times be “Is Torrenting Secure?”
The truth is, torrenting is a wonderful file-sharing service, utilizing peer-to-peer expertise to make commonplace file servers out of date.
Sadly, some irresponsible customers make use of BitTorrent’s benefits to share copyrighted materials and even malware.
Nevertheless, the protocol itself just isn’t chargeable for such actions, and I’ve seen many authorized companies utilizing torrents to share their information.
As a matter of truth, torrenting has executed extra without cost and open-source software program distribution than it has for piracy.
How Torrenting Works
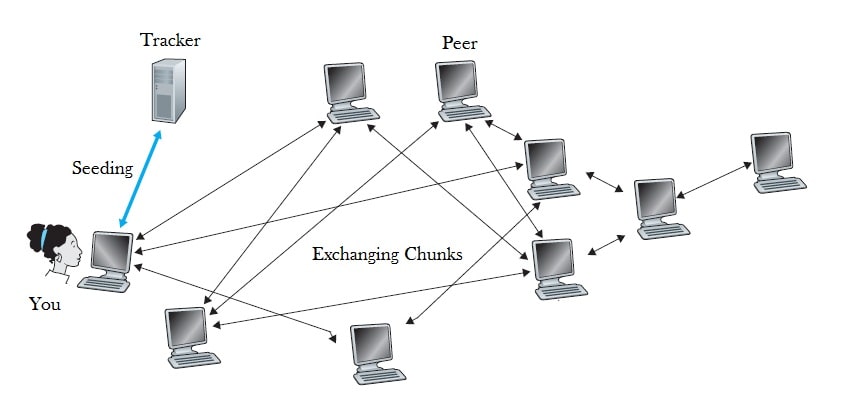
As I beforehand talked about, torrenting is a peer-to-peer file-sharing methodology.
It permits two or extra computer systems to ship information to one another over the Web, with none third social gathering in between.
In a approach, it’s like sending information between computer systems in an area space community, solely unfold all the world over.
While you obtain a file utilizing a torrent, you begin seeding it.
Seeding a file (or part of it) signifies that you’re sending it to all the opposite customers within the community who need to obtain it.
That approach, every one that downloads a torrent file has a task in sharing it additional.
The extra standard a torrent file is, the simpler and sooner will probably be for us to obtain it.
To maintain all the file sharing course of so simple as attainable, the BitTorrent protocol has a few providers to help it.
For one, you’ll want to have a torrent shopper with the intention to connect with the community. I counsel BitTorrent or QBitTorrent, however that’s as much as you.
Then, you’ll want to discover a torrent file or a magnet hyperlink to the file you need to obtain.
A torrent file is a small textual content file that incorporates the addresses of all of the computer systems at present sharing the file.
A magnet hyperlink is only a torrent file shortened all the way down to a URL hyperlink.
Torrenting vs. Conventional Downloading
Most individuals obtain information by their browser, utilizing a standard client-server connection.
While you begin a standard obtain, it establishes a connection between your laptop and the file server closest to your location.
Then, the server begins transferring the file to your laptop.
Sadly, the switch course of itself has a number of points.
For one, if the connection will get interrupted for any purpose, all the switch is canceled and you need to begin over.

I’m certain we’re all very conversant in the screenshot above.
Subsequent, your obtain pace is proscribed to the pace of the server. If the server is busy or far-off from you, you’ll discover your obtain pace dropping significantly.
To my shock, ExpressVPN boosted my add pace by almost 10%.
As well as, a file server wants upkeep, which has to return out of anyone’s pocket.
So, if the corporate internet hosting the file decides to tug the plug, the file received’t be obtainable for obtain anymore.
To get round these issues, the BitTorrent community splits every file right into a collection of small, similar items.
Then, every laptop within the community downloads the file piece by piece. That approach, the switch can cease at any time with no knowledge loss.
As well as, when a pc downloads a bit, it robotically begins sharing it with all different computer systems on the community.
So, every peer turns into a seeder even earlier than they end downloading a file.
On high of that, a file on the torrent community is out there for obtain so long as there’s a pc seeding it someplace.
After all, the pace relies on the add pace of the seeder. Nonetheless, two or three seeders will likely be greater than sufficient to maintain the pace up.
Why Individuals Use Torrents
Naturally, an nameless, easy, and efficient file switch methodology gained lots of reputation with web piracy fans. I’ve seen pirated films, TV reveals, video video games, software program, and rather more on unlawful torrent websites.
Extra or so, torrent film searches can be the highest precedence when folks consider torrenting.
Additional on, I’ll discover what authorized and technical dangers you may encounter when you use the BitTorrent community for downloading pirated information.
So, if piracy is out of the query, what do folks use torrents for?
Nicely, due to its scalability, simplicity, and strong implementation, many free and open-source builders use BitTorrent to share out their software program.
That approach, customers can help the developer’s work by sharing their software program and lowering their server prices.
I’ve additionally seen universities all the world over utilizing torrents to distribute giant quantities of information to their researchers.
As well as, a number of on-line video games use BitTorrent to distribute and replace them, relieving their servers from a lot of the workload wanted to distribute a sport to numerous gamers.
Lastly, even Microsoft makes use of the same service to distribute Home windows updates.
With all that in thoughts, it’s no shock to us that peer-to-peer sharing accounts for greater than 20% of all Web site visitors.
To place issues into perspective, it has extra community bandwidth than Netflix, Hulu, and Prime Video mixed, with lots of of hundreds of thousands of lively customers daily.
Is Torrenting Authorized?
Many individuals consider that torrenting is unlawful, which isn’t fully true.
All of it relies on the file you’re downloading.
Specifically, torrenting is simply one other file-sharing methodology, and it’s not unlawful per se.
Nevertheless, if the file being downloaded is restricted, i.e. protected by copyright legal guidelines, then the act of torrenting that file is taken into account unlawful, and I name it piracy.
As an illustration, pirates have their methods of snatching new episodes of operating TV reveals and releasing them to the general public.
So, as a substitute of paying for a Netflix or Hulu subscription, folks can obtain and watch their favourite TV reveals without cost.
Though that does sound interesting, it’s nonetheless copyright infringement, and it most actually is unlawful.
Naturally, firms that personal mental property need to be sure that it’s not being distributed unlawfully.
That’s why the Netflix VPN ban was within the first place.
That’s why they usually rent copyright trolls to search out and sue people who distribute their property with out their authorized permission.
I counsel that you just test your nation’s copyright legal guidelines to be sure you’re not unintentionally breaking any of them.
Torrenting Dangers
Apart from authorized points, there are a number of different dangers that torrent customers take with every obtain:
1. Malware
As I discussed, torrenting is all about sharing amongst friends, with no third social gathering being concerned.
That being mentioned, some information can comprise viruses, which I’ve no approach of understanding earlier than truly downloading the file.
And I don’t must inform you why malware is unhealthy — it messes along with your laptop, inflicting it to lag and carry out all types of unusual, undesirable duties (sending spam mail to everybody you recognize, opening and shutting packages, and so on.).
As a way to shield your laptop, be sure you use an antivirus program and scan each file after downloading it.
After all, if this system detects a virus risk, do away with the file instantly.
After all, some VPN suppliers do present some additional safety to their VPN customers in these circumstances as they’re properly conscious of the risk.
As an illustration, NordVPN with their CyberSec or Surfshark CleanWeb.
2. Vulnerability to Hackers
Though torrenting just isn’t sometimes harmful, it may be a useful gizmo for hackers to search out their “victims,” i.e. weak customers from whom they’ll steal info.
They achieve this by looking the IP addresses of all present friends one after the other till they discover the best goal.
Though IPv6 is safer than IPv4, nobody is adopting it.
To be sure you’re not the following sufferer of a cyber-attack, you need to scan your laptop for viruses frequently, flip off folder sharing, and set passwords for folders containing essential knowledge.
Or simply get a trusted VPN and all of your on-line actions will likely be protected.
As I’ve at all times mentioned, Keep Stealth, Keep Secure!
3. Information Theft
One other concern that torrent customers may need is knowledge security.
Allegedly, friends that you just’re sharing a file with can entry different knowledge in your laptop.
Nevertheless, that may solely occur if delicate knowledge is saved in the identical folder because the file you’re sharing, which isn’t that frequent.
Enterprise homeowners are sometimes those who’ve this concern, as they’ve many workers utilizing the corporate’s computer systems that comprise important knowledge.
So, if one of many workers makes the rookie mistake of saving the whole lot in a single folder, which could compromise the protection of the corporate’s knowledge.
Learn how to Keep Secure When Torrenting
As a way to be sure you’re torrenting safely, there are some things you need to do:
1. Keep Away from Unlawful Content material
As I mentioned, distributing and downloading another person’s mental property is unlawful.
Subsequently, doing so may result in some authorized costs.
3 Singaporeans had been fined $5000 for downloading a Hollywood film illegally. Although issues might get otherwise if they’d used a VPN in Singapore.
To forestall such inconveniences, you need to keep away from downloading unlawful content material altogether.
2. Use a VPN
VPNs are all the fad these days, and it’s straightforward to see why we’d like a VPN.
They’re extremely low-cost and simple to make use of, but they preserve you secure from prying eyes.
Along with defending your knowledge from hackers, in addition they cover the site visitors out of your web service supplier.
What a VPN does is “tunnel” your web site visitors by one other laptop far-off. As well as, most providers encrypt the connection.
That approach, all they’ll see is your laptop speaking with a VPN server, with no method to uncover what you do on-line.
Clearly, VPN’s effectivity extends past torrenting.
For instance, VPN may even let you’ve gotten entry to content material, movies, TV reveals, and films which were blocked in your nation.
3. Select Recordsdata and Trackers Rigorously
As a way to keep away from hackers and copyright trolls, be sure you at all times obtain torrents from a good supply.
In different phrases, select well-known public trackers which have many customers, as they’re a lot much less dangerous.
Top-of-the-line methods to remain secure when torrenting is to make use of a non-public tracker.
Discover a number of reliable ones, register with them, and also you’ll be set for a very long time.
Learn how to Torrent
1. Discover and Obtain the Torrent Consumer
In case you don’t have one but in your laptop/system, you need to lookup and obtain a good torrent shopper to handle all of your downloads.
BitTorrent and QBitTorrent are by far the most well-liked. They’re additionally utterly free, so I positively counsel giving them a go.
Clearly, you’ll be able to’t obtain a torrent file with out the shopper, however there are a number of extra benefits to having it.
As an illustration, a shopper can assist you simply handle the add and obtain course of. You possibly can pause it, cease it, resume it, in addition to prioritize and choose information inside.
What’s extra, you will discover different helpful data there, such because the estimated obtain time, add, and obtain pace.
Lastly, you too can see the addresses and areas of all of the units at present sharing the torrent.
2. Discover and Obtain a Torrent File
As I mentioned, you’ll want to watch out when selecting your tracker and information.
Use both a non-public tracker or a famend public one to attenuate the dangers of hacker assaults.
Additionally, at all times double-check the file you’re downloading.
A secure file will sometimes have loads of seeders and good critiques.
Obtain the .torrent file to your laptop or open it immediately within the shopper utilizing a magnet hyperlink.
3. Open the File within the Consumer
After that, the one factor left to do is select the vacation spot, i.e. the place you need the file or folder to finish up after downloading, and that’s it.
As soon as you choose “OK”, the file will begin downloading immediately.
The pace of the obtain will rely in your web connection, in addition to the variety of present lively seeders.
Greatest Torrent Search Engine Web site
Whereas there are lots of torrent search websites on the market, most of them didn’t reside as much as their guarantees.
Listed below are some that aren’t simply respected torrent search engines like google however are literally working on the time of my writing.
Whereas the remainder of the torrent search web site is both damaged when I attempt to entry it or there was a scarcity of seeds.
1. Torrents.me2. The Pirate Bay3. Torrents.io4. Xtorx.com5. YTS.mx6. Torrentz2.eu7. Toorgle
All of it goes again to the fundamentals and customary sense; I normally head to the place the crowds are.
Extra seeds, sooner pace, and likewise a safer group.
For a starter, most free VPN doesn’t help torrenting, overlook about them.
Nonetheless, nothing beats having safety upfront with a trusted VPN.